Com Ubuntu Apport Apport Gtk Root
Available languages:Italiano,
Contents
- What is this all nigh?
- What does it look similar for users?
- Why is apport disabled by default?
- How to enable apport
- I'chiliad a developer. How do I apply these crash reports?
- Study format
- Fields
- Tools
- Study format
- How does it work internally?
- Crash interception
- Case
- Backend
- Frontend invocation
- Crash interception
- Launchpad-based auto-retracer
- Per-package Apport Hooks
- Utilise the source, Luke!
- Future plans
- Further links
What is this all almost?
Debugging plan crashes without whatever automated tools has been pretty time consuming and hard for both developers and users. Many program crashes remain unreported or unfixed because:
- Many crashes are not easily reproducible.
-
End users practise not know how to prepare a report that is really useful for developers, like building a package with debug symbols, operating gdb, etc.
- A considerable role of bug triage is spent with collecting relevant information well-nigh the crash itself, packet versions, hardware compages, operating arrangement version, etc.
- There is no easy frontend which allow users to submit detailed problem reports.
- Existing solutions like bug-buddy or krash are specific to a particular desktop environment, are nontrivial to conform to the needs of a distribution programmer, practise not work for crashes of groundwork servers (like a database or an email server), and do non integrate well with existing debug packages that a distribution might provide.
Apport is a system which:
- intercepts crashes right when they happen the first time,
- gathers potentially useful data about the crash and the OS environment,
- tin be automatically invoked for unhandled exceptions in other programming languages (e. g. in Ubuntu this is done for Python),
- tin be automatically invoked for other problems that can be automatically detected (e. g. Ubuntu automatically detects and reports packet installation/upgrade failures from update-manager),
- presents a UI that informs the user most the crash and instructs them on how to proceed,
- and is able to file not-crash problems reports about software, so that developers even so go information about bundle versions, Bone version etc.
We are sure that this will atomic number 82 to a much better level of quality assurance in the future.
If you want to make crash reports of your software even more useful when being reported through apport, please come across /DeveloperHowTo.
What does information technology await like for users?
The user side of apport is designed to be extremely simple and equally unannoying as possible.
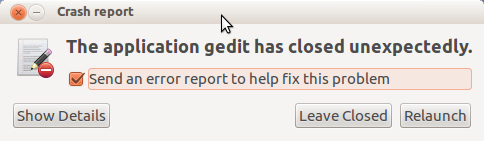
If any procedure in the organization dies due to a bespeak that is normally referred to equally a 'crash' (segmentation violation, autobus mistake, floating point exception, etc.), or e. g. a packaged Python application raises an uncaught exception, the apport backend is automatically invoked. It produces an initial crash report in a file in /var/crash/ (the file proper name is composed from the name of the crashed executable and the user id). If the crashed process belongs to the user who is currently logged in, or it belongs to a system process and the user is an administrator, apport informs the user near the crash and offers to written report the problem:
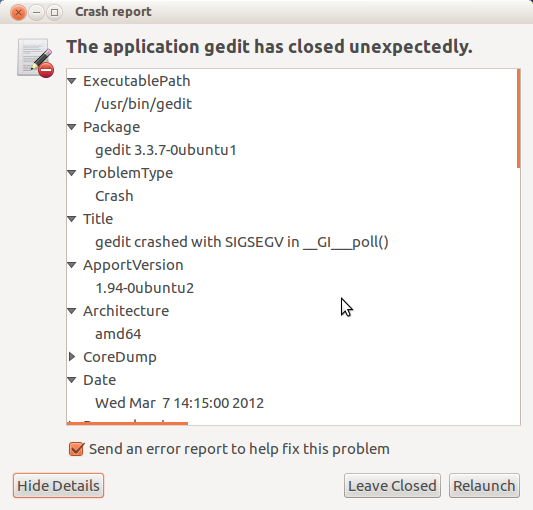
Y'all can click on "Show Details..." to see what data it collected:
If the user leaves the "Send mistake study" checkbox enabled, Apport uploads the nerveless information to the bug tracking system. After that information technology opens the packages' bug filing page with a sensible default bug title and leaves the residual of issues filing procedure to the web UI.
Why is apport disabled by default?
Apport is not enabled by default in stable releases, even if it is installed. The automatic crash interception component of apport is disabled by default in stable releases for a number of reasons:
- Apport collects potentially sensitive data, such as core dumps, stack traces, and log files. They tin can incorporate passwords, credit menu numbers, series numbers, and other private material.
This is mitigated past the fact that it presents you what will be sent to the problems tracker, and that all crash study bugs are private by default, express to the Ubuntu issues triaging team. Nosotros tin reasonably look developers and technically savvy users, who run the development release, to be aware of this and approximate whether it is appropriate to file a crash report. Only nosotros shouldn't assume that every Ubuntu user of stable releases is able to do so. In 12.04 and up this is transparently handled by whoopsie, see ErrorTracker.
- During the development release we already collect thousands of crash reports, much more than than we can ever fix. Continuing to collect those for stable releases is not actually useful, since
- The most important crashes have already been discovered in the development release.
-
The less important ones are non suitable for getting fixed in stable releases (see https://wiki.ubuntu.com/StableReleaseUpdates
- Request users to transport crash reports to us is insincere, since we can't possibly reply and deal with all of them.
- Information collection from apport takes a nontrivial amount of CPU and I/O resource, which slow downwardly the estimator and don't allow you to restart the crashed programme for several seconds.
Notation apport does not trap SIGABRT signals. If you lot are getting such a indicate, then please run across DebuggingProgramCrash.
How to enable apport
Apport itself is running at all times because information technology collects crash data for whoopsie (see ErrorTracker). However, the crash interception component is still disabled. To enable it permanently, do:
sudo nano /etc/apport/crashdb.conf
... and add a hash symbol # in the kickoff of the following line:
'problem_types': ['Problems', 'Parcel'],
To disable crash reporting just remove the hash symbol.
I'k a developer. How do I apply these crash reports?
Report format
apport internally uses the standard Debian control syntax for reports, i. e. keeps everything in a flat file that looks like this:
DistroRelease: Ubuntu 12.04 ExecutablePath: /usr/bin/gcalctool Package: gcalctool 5.8.24-0ubuntu2 ProcCmdline: gcalctool ProcEnviron: SHELL=/bin/fustigate PATH=/usr/sbin:/usr/bin:/sbin:/bin:/usr/bin/X11:/usr/games LANG=de_DE.UTF-viii StackTrace: [...] #0 0x00002ae577bb37bf in poll () from /lib/libc.so.6 No symbol tabular array info bachelor. #ane 0x00002ae57786991e in g_main_context_check () from /usr/lib64/libglib-two.0.so.0 No symbol tabular array info available. [...] CoreDump: base64 eJzsXQmcFMXV7+XGA0dBREVoDxSPXQYEB...
But a tiny subset of the available fields are shown here. Apport reports include a core dump in a compressed and encoded format, which is useful for post-mortem debugging and post-mortem generation of a symbolic stack trace.
Yet, when uploading the data to a bug tracking system, a unlike format tin be used. e. g. when using Launchpad, the data is uploaded in Multipart/MIME format so that the small parts land directly in the bug summary and the large parts become separate problems attachments.
Fields
Some fields warrant further details:
-
SegvAnalysis: when examining a Segmentation Mistake (signal 11), Apport attempts to review the exact machine instruction that caused the fault, and checks the programme counter, source, and destination addresses, looking for any virtual retentivity address (VMA) that is outside an allocated range (as reported in the ProcMaps attachment).
-
SegvReason: a VMA can exist read from, written to, or executed. On a SegFault, one of these 3 CPU actions has taken place at a given VMA that either non allocated, or lacks permissions to perform the activeness. For instance:
-
SegvReason: reading Nix VMA would mean that a Zippo arrow was most likely dereferenced while reading a value.
-
SegvReason: writing unknown VMA would hateful that something was attempting to write to the destination of a pointer aimed outside of allocated retentiveness. (This is sometimes a security issue.)
-
SegvReason: executing writable VMA [stack] would mean that something was causing code on the stack to exist executed, merely the stack (correctly) lacked execute permissions. (This is almost always a security issue.)
-
There are several tools available for working with a crash report:
-
Ubuntu Issues Patterns: These are patterns for packages (writable past Ubuntu Bug Control) that prevent bugs from beingness filed past apport. Complete details are found in the README.
-
apport-unpack: Unpack a report into single files (1 per attribute). This is nigh useful for extracting the cadre dump. Please see the manpage for further details. This tool is non necessary when working with Launchpad, since it already splits the parts into carve up attachments.
-
apport-retrace: Regenerate stack traces of a study. If you supply the -k selection, this tool will automatically download bachelor debug symbol packages and use them to generate a symbolic stack trace. The manpage explains the functionality and all available options in detail.
-
python-trouble-report: This package ships a Python module problem_report which provides general dictionary access to a crash report and loading/saving methods (not specific to apport reports).
-
python-apport: This ships a Python package apport which encapsulates cadre functionality of apport and is specific to crash and problems reports. You can utilize information technology to implement your own frontends and backends.
-
apport-collect: This checks the source parcel(south) of an existing Launchpad problems, runs apport hooks for them, and uploads their nerveless data back to the bug written report.
How does information technology work internally?
Crash interception
Apport uses /proc/sys/kernel/core_pattern to straight pipe the core dump into apport:
$ cat /proc/sys/kernel/core_pattern |/usr/share/apport/apport %p %due south %c $
Note that even if ulimit is set to disabled core files (by specyfing a core file size of zilch using ulimit -c 0), apport will withal capture the crash.
For intercepting Python crashes it installs a /etc/python*/sitecustomize.py to call apport on unhandled exceptions.
Instance
Apport is fifty-fifty able to capture core files if PID 1 (Upstart) dies:
-
If Upstart detects an internal inconsistency, it raises the SIGABRT signal.
-
The Upstart crash handler is called on SIGABRT.
- Upstart crash handler forks a child process.
- The Upstart child procedure re-raises the signal which results in the kid exiting abnormally.
-
The kernel detects the child process has exited abnormally and calls apport, pipe the core file to apports standard input (due to /proc/sys/kernel/core_pattern).
-
apport writes the core file to disk in /var/crash/.
-
PID 1 waits for its child to terminate (which only happens in one case apport has finished writing the cadre file).
- PID one exits.
- kernel panics.
- On adjacent boot, Whoopsie volition detect the crash file and process it.
Backend
In lodge to keep the delay and CPU/IO bear upon as low as possible, /usr/share/apport/apport only collects data which has to be acquired while the crashed procedure still exists: information from /proc/ pid, the core dump, the executable path, and the betoken number. The report is written to /var/crash/ executable_path . uid .crash.
Frontend invocation
In Gnome, update-notifier keeps an inotify watch on /var/crash. Whenever at that place is something new, it calls /usr/share/apport/apport-checkreports. If there are new reports, it calls /usr/share/apport/apport-gtk, which is the frontend shown in the screenshots above.
The frontend then collects additional information like bundle versions, bundle file checksums, or Bone version, and calls all matching bundle hooks.
To disable this, you can run gsettings set com.ubuntu.update-notifier show-apport-crashes false (equally your ordinary desktop user).
Launchpad-based car-retracer
The Approved information middle runs a service which automatically retrace bugs with apport. By tagging the bugs co-ordinate to compages in Launchpad, a retrace will be done and the tag will exist removed. Tags that are used are demand-i386-retrace or need-amd64-retrace. Come across the annunciation.
Per-package Apport Hooks
It is possible for packages to specify information gathered from the system and included in the bug written report. These are done by apport hooks contained in packages. For some useful examples see:
- source_xorg.py - adds additional log files and hardware details to bug reports
- usplash - ignores crashes in specific lawmaking paths
- source_totem.py - asks the reporter questions and gathers unlike data based on responses
in /usr/share/apport/parcel-hooks. In that location is also a list of packages providing apport hooks.
Please see /DeveloperHowTo for further information.
If a crash or bug report is submitted through apport, the relevant hooks will be run automatically. If you have an already reported bug that was filed without apport, and y'all are interested in the information from those hooks, you tin can enquire the bug reporter to use apport-collect bugnumber (run into #Tools).
Use the source, Luke!
-
Y'all can download the upstream tarball from the Launchpad project page, or the Ubuntu source tarball from the Ubuntu archive.
-
apport is developed with the bazaar RCS on Launchpad. If y'all want to contribute to it or develop your ain system based on it, y'all tin can get your own branch with bzr branch lp:apport for trunk, or debcheckout -a apport for the Ubuntu packaging branch.
You lot can too browse it online.
Future plans
-
Various improvements to performance, better tools to work with reports, and integration of more than languages (Mono/Python stack traces, assertion messages, etc.) See the relevant specification.
Farther links
-
The study file data format specification.
-
Original specifications: apport design, User interface
-
Ubuntu apport problems patterns
-
Whoopsie is a newer Ubuntu crash submission system that doesn't require any input from the user and integrates with Apport
-
Please practice not hesitate to study bugs and characteristic requests to the bug tracker.
-
See Bugs/ApportRetraces for additional documentation for those triaging Apport-generated bug reports in LaunchPad, based on a MOTU/School session by EmmetHikory .
-
Brian Murray gave a class at Ubuntu Programmer week regarding writing bundle hooks.
-
Integration using LaunchpadIntegration: https://wiki.ubuntu.com/UbuntuDevelopment/Internationalisation/Coding#LPI
Apport (last edited 2017-05-25 20:03:48 by penalvch)
Source: https://wiki.ubuntu.com/Apport
Posted by: howardsciallsolle.blogspot.com

0 Response to "Com Ubuntu Apport Apport Gtk Root"
Post a Comment